In this post we will try to analyze Teams call flow using Wireshark tool. For this demonstration we will take 2 users (User1 & User2). User1 will try to establish call with User2 and based on their location (direct connection, behind NAT Or behind Symmetric NAT etc…) we will see & try to analyze the traffic flow. User1 will make a call to User2 and below set of action will happen for complete P2P call establishment.
User1 will approach O365 Teams/STUN server to get the list of ICE candidate. User1 Teams will send below STUN request on UDP port 3478.
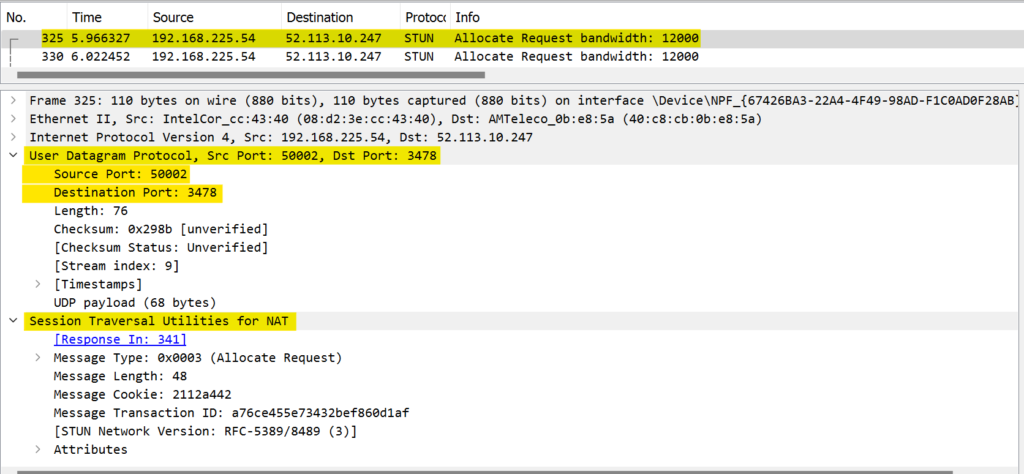
STUN server will respond back to User1 with server reflexive IP. In our case, STUN server had received the request from User1 PC with IP address as (169.149.227.137:50002). Next in a Success response, STUN server will respond back to User1 with srflx IP address aka XOR-MAPPED-ADDRESS. In below screenshot we can see the reflexive IP as XOR-MAPPED-ADDRESS.
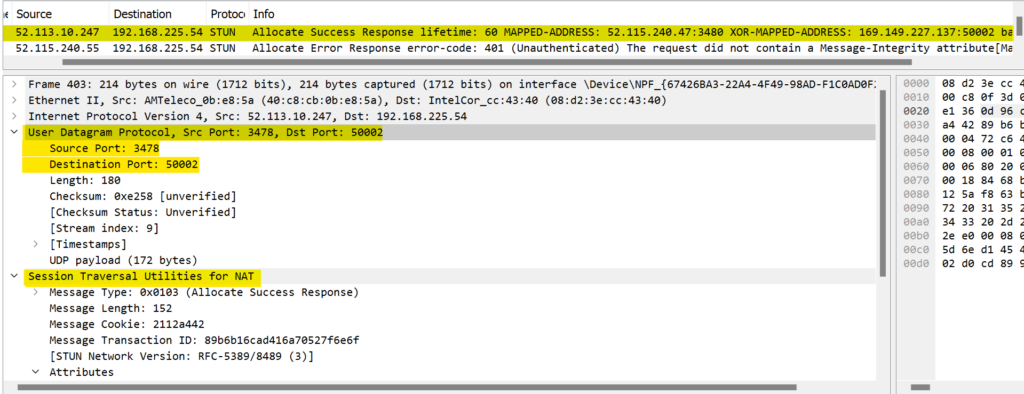
Once User1 PC received Success response from STUN server. It will draft Offer for User2. This is basically a SDP offer from User1 to User2. In this offer User1 will encapsulate the list of all ICE candidate and send it across to user2. Below is the list of ICE candidate onto the SDP offer from User1.
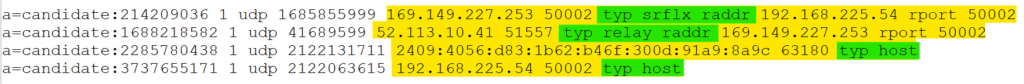
host: This is User PC private address both IPv4/IPv6 e.g. 192. OR 10. series.
srflx: This is User1 public IP address to reach him directly for P2P connection.
relay: In case User1 is not reachable directly via srflx IP. Then he can be reached via relay
Once User2 received the SDP offer from User1, it will come to know that User1 is reachable at (169.149.227.137:50002). User2 will follow same process just like User1 and share his details (20.169.147.150:50006) with User1. Once both the users knows other endpoints IP Address:port RTP communication will start.
Last we checked the RTP stream and we were able to see User1 & User2 are communicating directly to each other on shared reflexive IP addresses they obtained from STUN server.
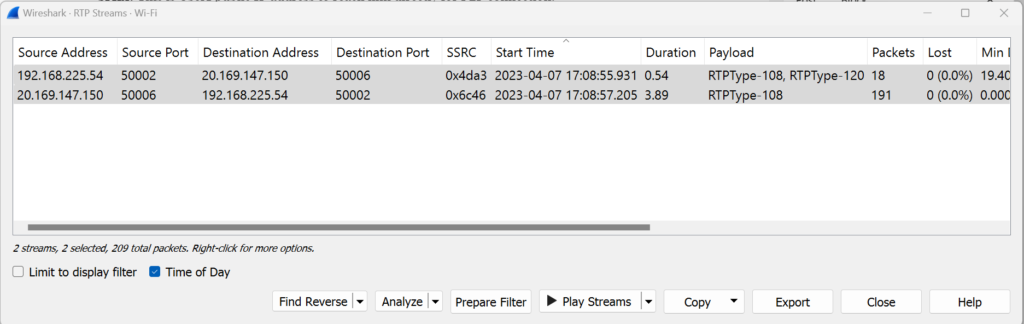
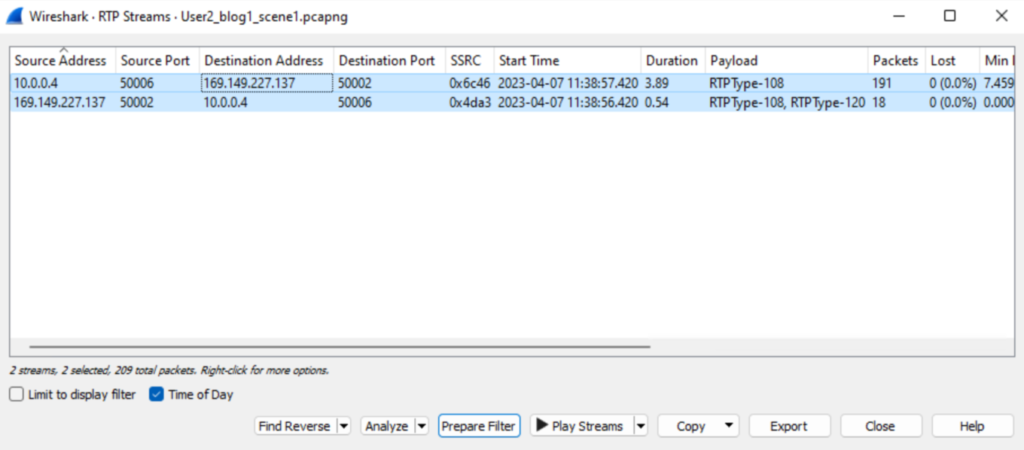
Very important to note, in this case users were able to communicate directly with each other over 50000 port numbers using srflx IP addresses because they are in less restricted NAT environment on both the side. Next we will discuss the call flow when Teams users can’t establish direct connection Or Symmetric NAT is in place and they make use of Transport Relay Or TURN servers.
Note: Onto RTP stream we are seeing 192.168 & 10.0 series IP address. These are the actual IP address of these PC and Wireshark capture is running on these NIC cards. So we are seeing these Private addresses.

This is best explanation I have ever come across. We were facing issue with call flow and this article really helped to narrow down the issue using wireshark.