This is most common method used to avoid interactive login & when you want to run an script in unattended mode. Let’s start by Registering an application in Azure.
Below are the steps to register an application in Azure AD:
- Sign in to Microsoft Entra admin center & expand Identity from left side blade panel.
- Next Click on Applications > App registrations, then on New registration
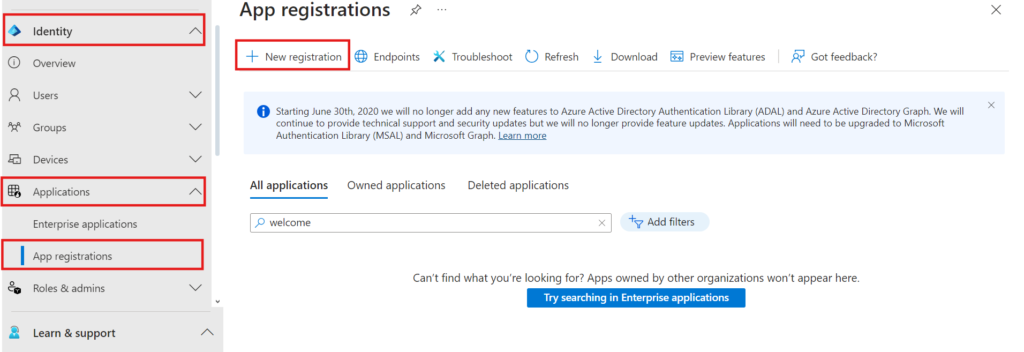
- Type any name you want to give, you can chose any name which is relevant to the app.
- We will use name MSGraph-CBA
- Select Accounts in any organizational directory (Any Azure AD directory – Multitenant) and personal Microsoft accounts & Register
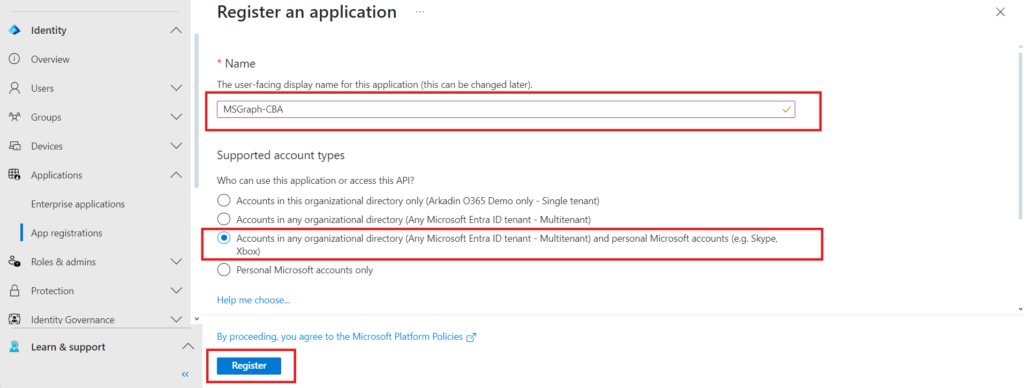
- Next you will see application overview for MSGraph-CBA application.
- Make note of the Application (client ID) and Directory (tenant) ID, we need them on later point of time.
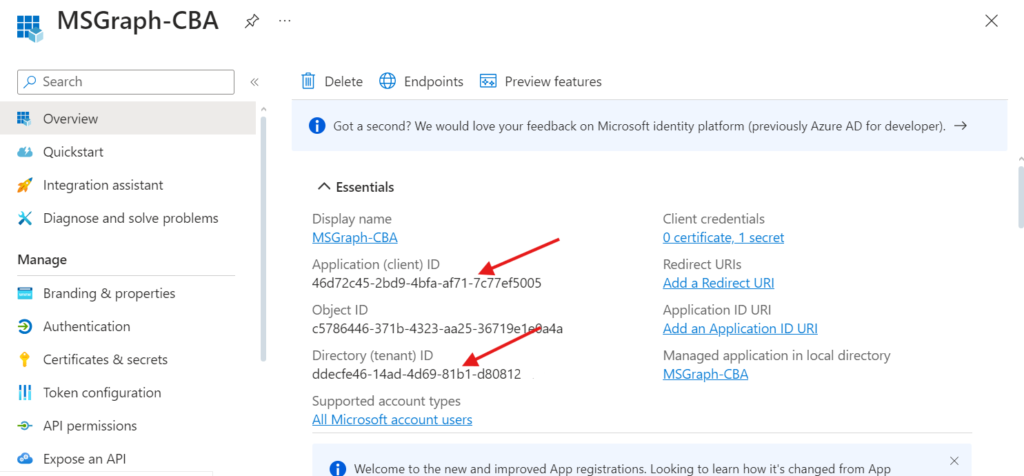
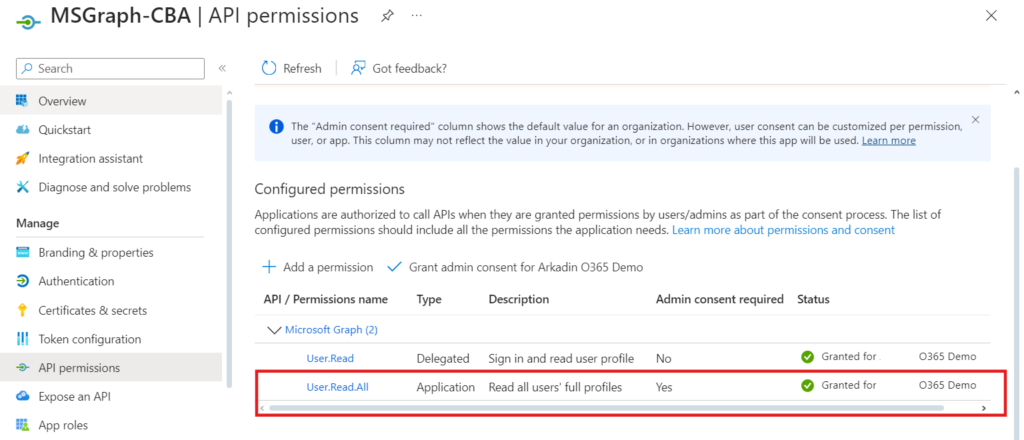
- Configure Azure application API permissions, we need to add API permissions to the MSGraph-CBA application we have created, by following the below steps:
- Click on API permissions > Add a permission
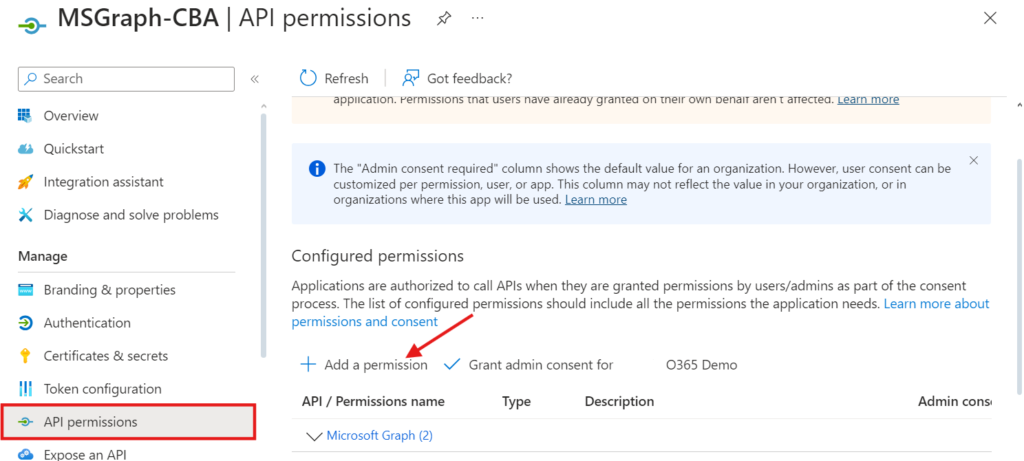
- Select Microsoft APIs > Microsoft Graph
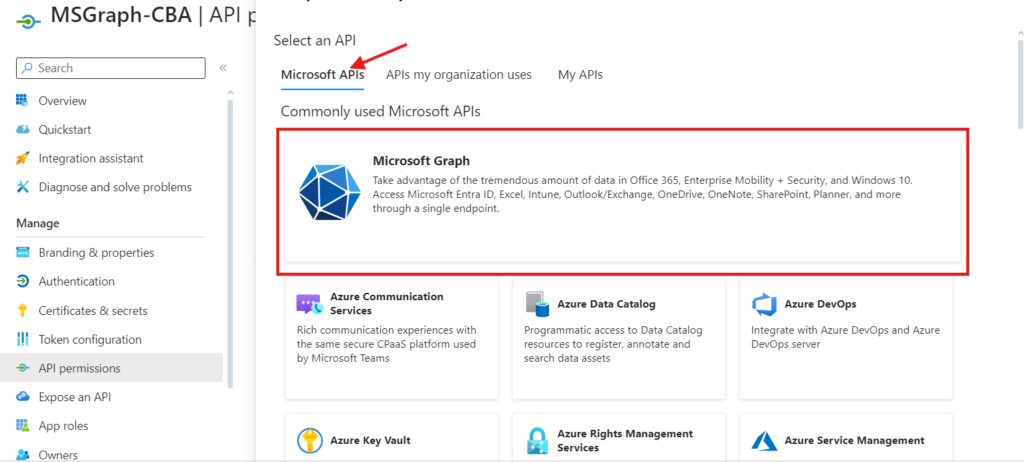
Select Application permissions
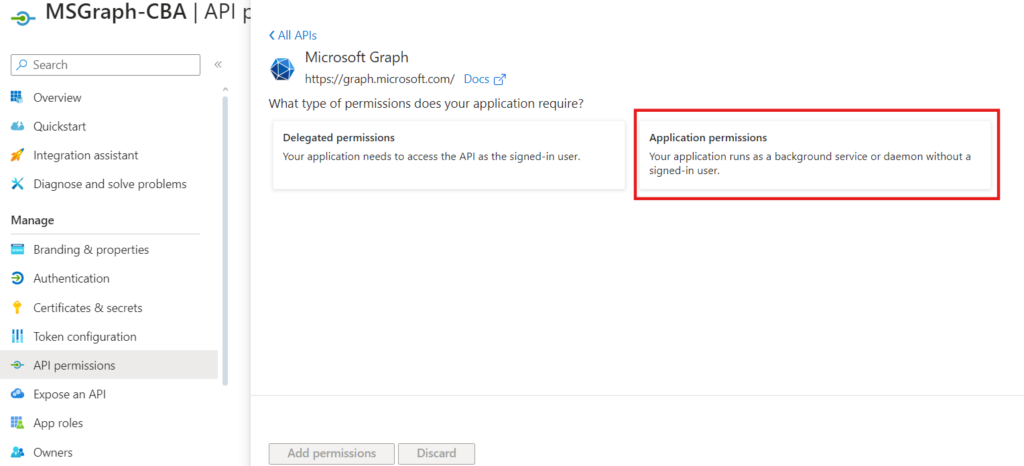
- Search for user.read.all
- Expand User and select User.Read.All
- Click Add permissions
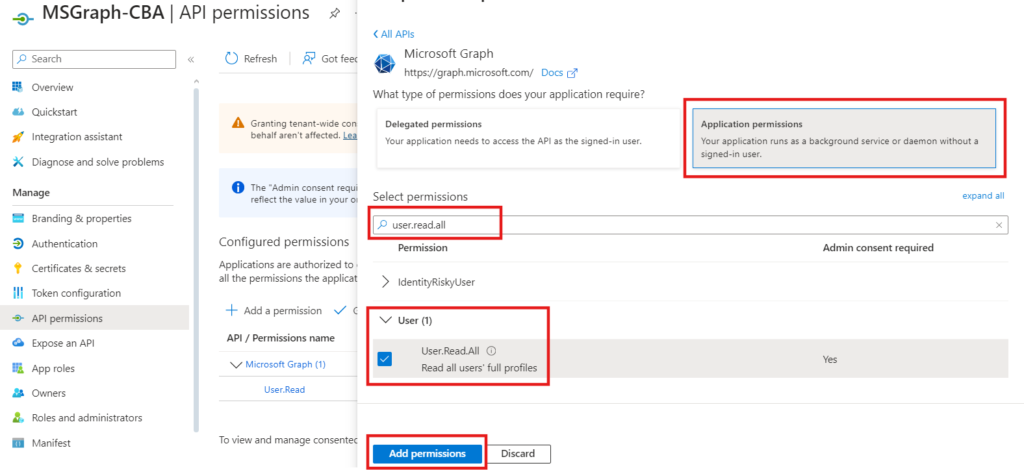
- Click on Grant admin consent
- Click Yes
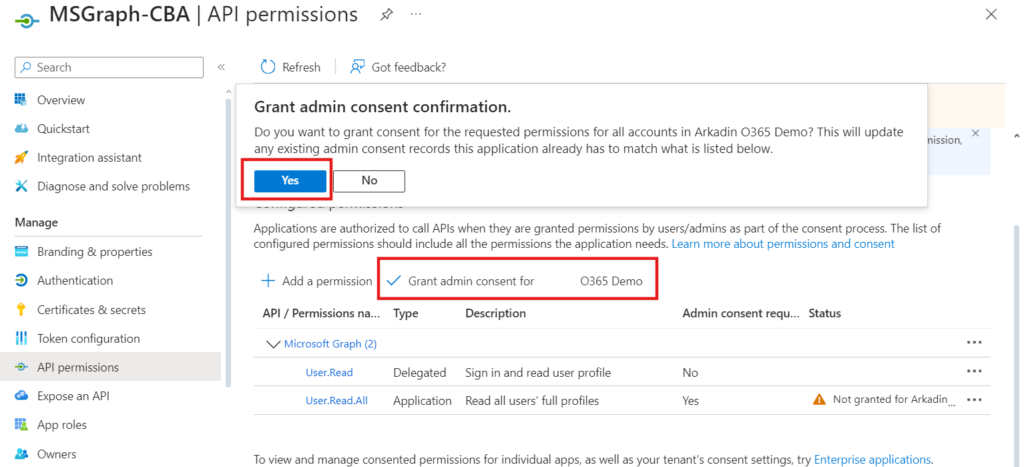
- The status shows a green checkmark
Now that the application is registered and the API permissions are set, we can configure two methods for authentication; Certificate or Client Secret. But we will be focusing on Client Secret based method.
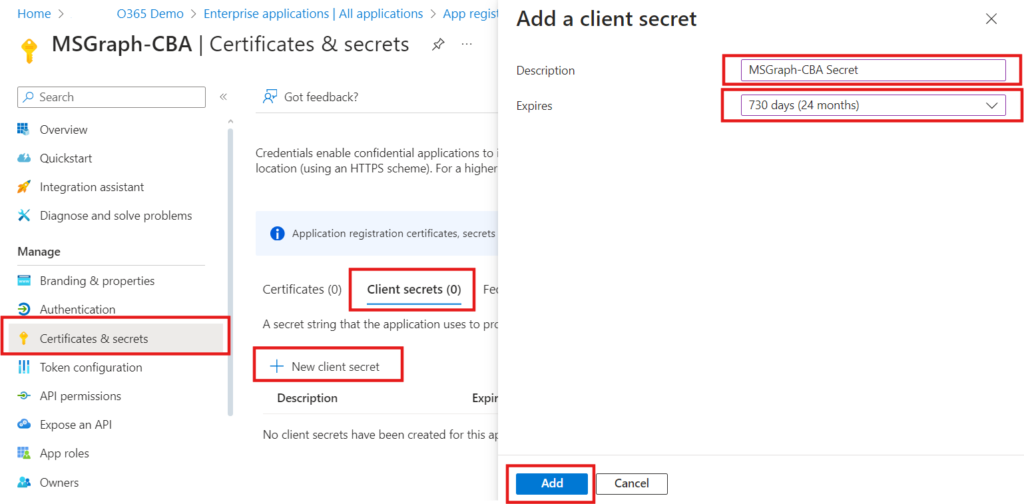
Client Secret !! Ok the last step, we need to add a Client Secret that the application uses to prove its identity when requesting a token from Entra ID.
- Click on Certificates & secrets
- Click Client secrets > New client secret
- Give it the description MS Graph CBA Secret
- Select the expires date 730 days (24 months)
- Click Add
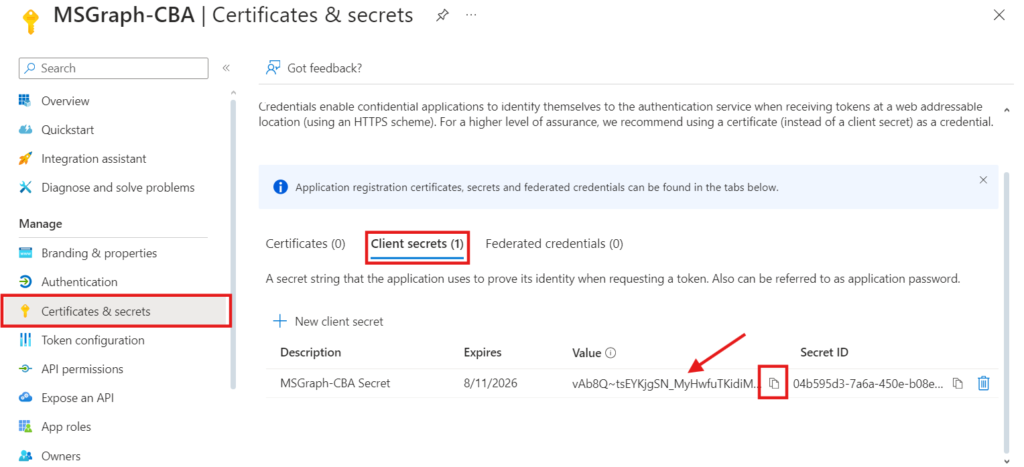
- Make note Client Secret Value we need it in the next step when connecting to Microsoft Graph
7. Connect to Microsoft Graph with Client Secret
Start Windows PowerShell and create below three variables to connect to Microsoft Graph PowerShell with Client Secret:
- $ClientId
- $TenantId
- $ClientSecret
# Configuration $ClientId = "46d72c45-2bd9-4bfa-af71-7c77ef5a" $TenantId = "ddecfe46-14ad-4d69-81b1-d8081230" $ClientSecret = "vAb8Q~tsEYKjgSN_MyHwfuTKidiMk5hniuk87n" # Convert the client secret to a secure string $ClientSecretPass = ConvertTo-SecureString -String $ClientSecret -AsPlainText -Force # Create a credential object using the client ID and secure string $ClientSecretCredential = New-Object -TypeName System.Management.Automation.PSCredential -ArgumentList $ClientId, $ClientSecretPass # Connect to Microsoft Graph with Client Secret Connect-MgGraph -TenantId $tenantId -ClientSecretCredential $ClientSecretCredential
Now that you are connected to Microsoft Graph PowerShell, run the Get-MgUser cmdlet to get the list of users.
Get-MgUser
Great !! That’s all
